
Identity fraud is older than the Insurance industry, so how can modern technology solve issues that are centuries old without alienating users or requiring 'police state' security measures?
As Elizabeth Greenwood's recent article on 'Faking your own Death' demonstrates, identity is a tricky business. In an era increasingly using modern forms of identity verification such as biometrics, it is interesting to consider their strengths and limitations. In the event of an unfortunate or faked demise, one's static biometrics such as fingerprint, retina pattern, facial likeness, etc. are all good indicators of individual identity, with DNA topping the list.
The problem with these static biometrics is that once these are known to fraudsters, they become easy to copy. To identity industry insiders, there are many high profile examples of each of these types being scammed, whether that is the German Prime Minister and Defence Minister both having their identities copied with sufficient likeness to fool high security military systems (one was by their fingerprints being modelled from high resolution photographs of their hands during a press conference, whilst the other was by agitating no more than a photograph of Angela Merkel in front of a facial recognition system to fool both likeness and liveness functionality).
As consumers are increasingly making use of fingerprint and facial recognition technologies shipped with devices such as mobile phones, tablets and PCs, the problem is set to intensify at an alarming rate. Worse, if copied, we cannot change our static biometrics (at least not without painful surgery). Once compromised, it is forever compromised.
Today's 'New' Biometrics
This is where behavioural biometrics come to the fore. Technologies such as signature, voice or even gait (the way we walk) are things that humans do in a manner that has a consistent pattern but also with sufficiently inconsistent variation if measured accurately enough to produce a different set of data points every time. For example, signature biometrics utilise one's X-Y visual signature graph formation through time but also track variables such as pressure, speed, acceleration, tilt angle, etc. - each up to 230 times per second per variable. When measured this accurately, no human signs identically on all data points.
However, we do sign consistently within patterns that hold true whether we are signing in a small, medium or large sized signing area on forms, documents and the like. It is this very human variation within our natural action patterns that adds a security level. The strength is that such behavioural or "dynamic" Biometrics cannot easily be forged. They present higher resilience, but also an important social advantage - people are used to signing to verify identity. Thus signatures are not perceived as intrusive in the manner that many static biometrics are, such as fingerprints (with police state connotations). This 'natural alignment to use case' is important for good customer experience.
For identity verification in the context of documents and forms, signature biometric approaches have many advantages. When it comes to verifying identity in call centre uses, such as with First Direct Bank, then voice comes into its own as a form of biometric to initially verify identity which is naturally aligned to customer behaviour in a non-intrusive but secure manner.
Biometric signatures have one more ace card in uses related to documents, whether for insurance claims or legal matters in the example. Since they are handwritten natural signatures, when recorded with the best eSignature technologies, such as SIGNificant, they have not only the highest level of legal admissibility but also much greater evidential weight in case of any dispute.
Forensic Biometric Analysis Deters Fraud
Forensic analysis of eSignatures, particularly such biometrically captured signatures, is much more useful than the analysis of ink-on-paper signatures given the level of detailed information contained within the signature. The forensic level of the eSignature's contextual data means that the levels of proof of the signature itself is extremely high and that such proof is bound to the documented content (such as a contractual agreement, or perhaps even a death certificate) with a full audit trail of the devices used for completion, location of use, date, time, image attachments, etc.
This self-contained 'evidence pack,' in the form of a PDF proves to be useful where claims arise. For the Italians using this technology tens of millions of times every month for financial and other important transactions, even the burden of legal proof has reversed! Italian courts have ruled previously that, provided the defending organisation can produce a PDF that has not been corrupted, the burden of proof moves to the claimant: they instead will have the onus of proving their case. Almost certainly, many false claims will have been deterred by this shifting of responsibility.
The Physical Limitations of Biometric Verification
The biggest problem with behavioural biometrics is that they cannot help in cases such as faked deaths. In that sense one's signature or voiceprint or gait is voluntary. These are things that each of us can change with practice. This is a double edged sword: it offers the ultimate protection if compromised by a forger - we can simply change it; The problem is that it cannot prove identity in the case of a faked death scammer's new identity (assuming they have changed their signature and that they have used other documents to reinvent themselves as a new, trusted customer on any system demanding the biometric). Nor can it prove identity from a corpse alone.
Hence biometrics such as signatures are "voluntary" in nature; good where we want something that we are happy to openly give for something in return. Whether organisations use much hated password and PIN combinations to prove identity, or modern biometric approaches, such a decision ultimately comes down to a balance of risk. No system in the world is infallible. The question is how much inconvenience would a customer have to endure in order to fool the system? As for the financial, reputational or other risk involved for the organisation, how much is it worth to protect against such risk versus possible incremental profits derived from offering a service with lesser protections?
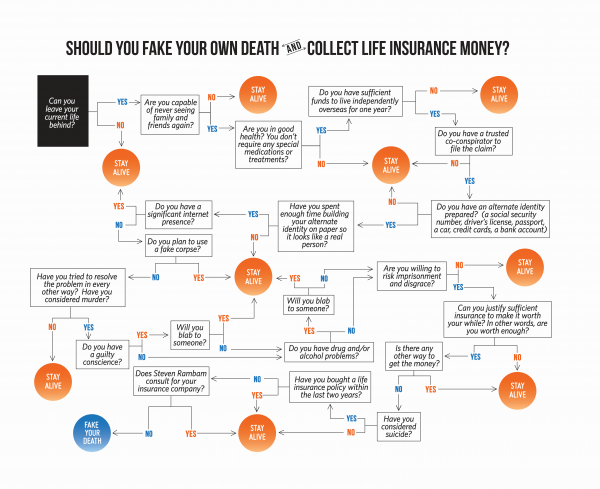
Biometric technologies are not a panacea. They cannot solve all identity issues and are not suitable for all use cases. It is critical that the right technology and method of implementation is aligned with natural behaviours, security, risk and customer preference. Multi-modal approaches combining different biometric technologies will be the way forward in many situations. After all, in Elizabeth's journey of discovery (as she mapped in "Should you fake your own death and collect life insurance money?", reproduced below), she came to realise that staying alive was really a very good balance of risk!
Chris Jones is the Managing Director of Icon UK, a specialist in Document-centric Identity Management.
click to enlarge:
|


 Connect with us on Linkedin
Connect with us on Linkedin 


 Connect with us on Linkedin
Connect with us on Linkedin 

![]()
![]()
![]()