Digital Transformations to
Eliminate Your Process Frictions


 Connect with us on Linkedin
Connect with us on Linkedin 
Call +44 (0)203 823 6535
or click here to arrange a callback
Signature Verification / Signature Authentication
(SIGNificant Biometric Server)
The SIGNificant Suite helps introduce your company to the era of handwritten digital signing with the most advanced signature biometrics. The SIGNificant products record the handwritten signature biometrics of a person (including measurements of parameters of pressure, acceleration, speed, rhythm, and movements in the air such as dotting "i"s) and embed the signature into an electronic document. If there is a dispute about a captured signature, an expert tool is available to forensically analyze the captured signature biometrics characteristics.
The SIGNificant Signature Verification technology, called "SIGNificant Biometric Server", takes this ability one step further, enabling real-time biometric verification of a signature to the SIGNificant platform by comparison of the recorded parameters of the handwritten signature biometrics against the pre-enrolled profile. The possibility of a detailed protocol for each signature-relevant action makes it a total solution; documents are only processed if their signers are authenticated and companies can prove who signed which document and when.
How It Works? - Three Easy Steps
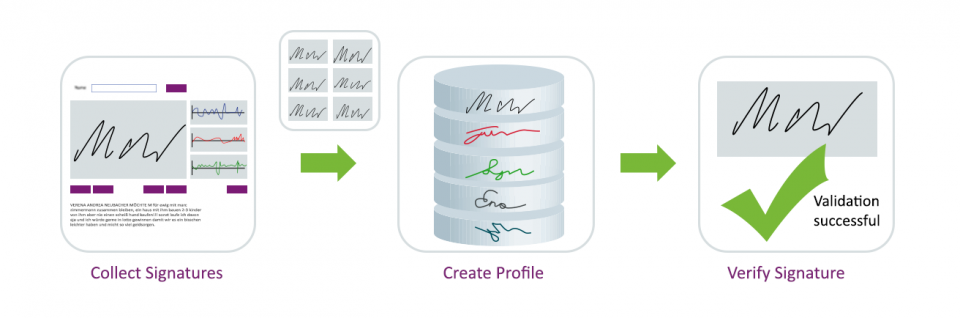
1. Enrolment (Collect Sample Signatures)
The process is initiated by the user’s enrollment. The enrollment process requires up to six initial signatures or can be done continually over time. These are collected using a signature pad or a tablet; the user simply signs his personal handwritten signature, exactly as he or she would with a wet-ink pen and ordinary paper.
2. Signature Profile Creation and Handling
The signatures are stored in profiles. The system can handle numerous profiles per user, allowing, for instance, for one profile for a standard signature and another for signing with initials only. When verifying a signature, the SIGNificant Biometric Server compares the signatures to the relevant profiles.
3. Signature Verification and Learning
Each time a user accesses the system to verify his signature, the Biometric Server compares the current signature biometrics to the signature profiles. With each authentication, the server continues to learn and fine-tune the user’s profile. This enables the system to track gradual shifts in the handwritten signature over time.
Forensic Signature Analysis tools (in case of dispute)
This short video illustrates how SIGNificant tools enable experts to most accurately determine the authenticity of a signature after the event.
Security Configuration
Signatures are the only biometrics that vary over time. Every biometric system, such as iris scan, fingerprints etc., may be hacked. Once hacked, the information may be used again and again because eyes, fingerprints etc., do not change (they are static). By contrast, a signature, even if hacked, is not reusable since no-one can ever sign exactly the same signature twice in the same manner; signature biometrics are bound to be different from one another when measured accurately enough as with SIGNificant. Also, even if the user suspects they may be compromised, they can always change a signature and create a new personal profile.
The SIGNificant Biometric Engine has three basic security modes that define how complex a personal profile has to be, and how strictly the Biometric Engine should verify the signature. The higher the security, the more likely it is that this customer subset will have to sign more than once before their signature is accepted. Thus the enrollment process becomes stricter for them, possibly requiring more than the initial 4-6 signatures needed for a standard enrollment.
- Basic - This setting is intended for scenarios where you expect large numbers of customers per day, and where you want to avoid having some users sign multiple times because of false rejections (FR), but still achieve reasonable security in the verification of signatures. Typically, this scenario suits processes where you want to enhance security or where you want to replace the signature comparison presently done by a human. In this case, these settings are a perfect fit for increasing the security dramatically whilst still having very high customer acceptance.
- Advanced - This setting is intended for scenarios where you expect large numbers of customers and skillful fraud attempts. Typically, this scenario suits processes where the signature has an important business impact (e.g. withdrawal of cash, signing important contracts etc.). Because of the importance of the signatures, you are willing to accept that some customers will have to sign more than once before the document is processed, to achieve better security against fraud.
- High - This setting is intended for scenarios where you expect very high security with medium to small numbers of customers. The security parameters allow for a near-zero percentage False Acceptance Rate; therefore this is suitable for even the most critical environments.
The major advantage over other solutions on the market today is that our technology is able to compare a signature against a profile which is self-learning over time. Only this dynamic approach guarantees appropriate results for signature verification and authentication, respectively, because it is human nature never to sign twice in exactly the same way, and also to alter the signature constantly over a life-time. Perhaps that's why SIGNificant was found to be the world’s most complete, open and accurate real-time signature verification technology. (Read more: SIGNificant wins international signature verification competition)
Additional Features
In addition to the general features described in the Overview section, Signature Verification functionality includes:
 |
Versatile Threshold |
 |
Automatic Detection |
 |
Dynamic Signature Verification |
 |
Clear, Fast Verification Results |
 |
Constant Profile Enriching |
 |
High-Security Concept |
 |
ISO/IEC 19794-7 |
 |
Audit Trail |
